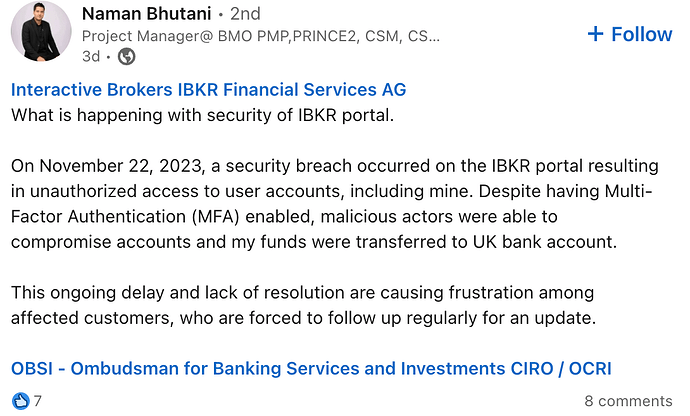
I have seen this post on Linkedin, which made me a bit worried.
What are the securities which can be activated (or you are using) to secure your IBKR account ? and limit unauthorized transfer ?
Link to the LinkedIn Post including fairly swift answers from IBKR’s LinkedIn company account.
I haven’t heard of an IBKR breach (which doesn’t mean much, of course, though I watch the security space and companies getting hacked pretty closely).
My personal experience of transferring funds and securities from my IBKR account even to my son’s also IBKR account required him and me authenticating to IBKR via passport, signed forms, a multi week review by their backend team, etc (all of this additonally just to authenticate and authorize the transaction after both IBKR accounts had already been set up by each of us with usual procedure of identifying via passport copies, etc etc).
Waiting to see the reply on this from IBKR but I’m spooked and questioning if / when I need to get my assets out of IBKR. If something like this happens I want my bank on the phone daily and not have to send tickets into an echo chamber
EDIT: I just changed my password, not sure whether it will help or not
I could not find any information online about a supposed leak on November 22, 2023.
- No press releases on IBKR: Press Releases | Interactive Brokers LLC
- No records on haveibeenpwned: Have I Been Pwned: Pwned websites
- Nothing on Reddit
If something like that would have happened, shouldn’t have been more than a single complaint?
Here are some tips on how you can secure your account on IB: How We Protect Your Account - Strength and Security | Interactive Brokers LLC
If your net worth is >$1M, then you can even request a pysical security card, didn’t know that… Secure Login with the Digital Security Card+
This is serious . I am wondering how is it possible to transfer funds to another bank account when MFA was activated.
I see following possibility.
- Account hacked
- Money transferred to IBKR from fake bank account (hacker’s account) which was created in name of person whose account was hacked
- Stocks sold
- Money transferred to the hackers account (#2)
This would need quick large scam. But I believe it is technically possible.
I am not sure how does IBKR check if account used for money transferred into IB is indeed an account from user
Wouldn’t one get a notification on the mobile aop, when there is a correct login with your username and password? I always have to confirm the login attempt in the app. How can a hacker fake this 2nd authentification?
Yeah this is something I don’t understand. This is only possible if IBKR was compromised and hackers were able to bypass their security process and hence also MFA.
I was more thinking about what happens after the account was hacked in terms of money transfer. Since they only transfer to your own bank account, one needs to engineer that part as well.
I get emails when I transfer money (in or out). But I suppose once hacked in, the email can be changed.
Also cash settlement should take 2-3 days when you sell securities but it could be picked up only if you receive app or email alerts.
Diversifying brokers could lower the risk of losing lifetime saving.
Applying Occam’s razor I would suggest a simpler explanation: the person got phished (including MFA) and that this is how the transfer was initiated. Even simpler: the claim is made up.
Couple of other things that don’t make sense to me:
- person claims multiple “user accounts” including his were compromised: how does he know of the other accounts that were supposedly compromised?
- why wait 100 days to follow up (as he claims the incident took place in November 2023)
a) via an IBKR ticket (the one referenced in the screenshot seems to be dated March 4 2024)
b) via LinkedIn a couple of days later (why not pick up the phone with IBKR?)
Anyhow, we can only speculate, but I’m not holding my breath that this is an IBKR compromise.
That was my first thought. Phished or scammed. Probably sent the MFA codes or had his MFA device hacked.
Probably worthwhile to consider whether you want your day to day phone as MFA to your IBKR account…
On the other hand, you get informed immediately, when there is a login attempt, when you have it on your main phone.
Well you can always carry both phones…
Errors and phishing could always happen.
What worries me is the apparent lack of urgency. My own experience with IB customer service is that my questions have been left answered on more than one occasion
Watching to see if the linked in post is updated tomorrow
He asks for an update in Dec which implies he followed up before then. I suspect the amount may not be large. Regardless I would expect my bank to update me on such a Q as a priority.
How do you implement this on IBKR?
In an Individual Account (and probably everywhere else) you can add users and give them roles with granular permissions.
Would you or any security experts have advice for the forum how to secure our IBKR accounts?
I access my account via the IBKR iphone App or the web interface. I have 2 Factor Authorization (password and phone). I have fingerprint ID enabled on my phone. I also have a level 3 card saved in a safe location.
I wonder how safe the fingerprint ID is
Digital Security Card+ is referenced above but from an internet search I am not sure that it provides additional security
p.s. still no response from IBKR to the Linkedin post…
I’ll open with that I won’t call myself a security expert given the security experts that I know, but if you ask all my friends and even some of my security expert colleagues, most would probably still stick that label on me.
This is just me saying that I know a bunch of people who know a lot more about car engines than I do, but most of my friends would still call me a seasoned car mechanic.
With this out of the way …
Your security precautions for accessing IBKR all sound reasonable to me.
Frankly, if you get compromised, I don’t think that it’ll be through a technical attack vector (a security vulnerability in any of the software/hardware you use) but through you unknowingly participating in a con operation, i.e. some more or less sophisticated scam (“IBKR is pro-actively reaching out to you to reset your password for security reasons, here is the secure link to do so: https://security.ibkr.com (when prompted, please confirm the new password through MFA)
The security of our users is at the highest priority at IBKR. Please follow these security instructions promptly.”)
If you wanted to step up your game, use a separate phone (can be an old one of yours) exclusively for accessing or authorizing access to IBKR.*
Ditto for browser access to IBKR: use a separate browser - e.g. Firefox/Edge/Safari instead of your standard Chrome browser (interchange those browser brands according to your personal setup) - that you exclusively use for accessing IBKR.* Bookmark the original URL for accessing IBKR in that exclusive separate browser and only access IBKR through your bookmark (versus following a link sent to you via email/chat/etc).
I used to do the latter (separate browser) in the early days of online Internet banking when I was still concerned mostly about the technical security of the software involved (I didn’t use any mobile app for Internet banking back in those days for the same technical security concerns).
I am still concerned about the technical security of the software involved, but I believe that as an ordinary person you’re now magnitudes more likely to fall victim to social engineering versus some elite hacker using technical zero-day software exploits.**
Fingerprint ID: I wouldn’t worry about it unless you know your phone is accessible to random people without your supervision lots of the time.
If you mainly have your iPhone in your posession and use the fingerprint reader to authenticate and to authorize things … well, you control access to those capabilities (even if the fingerprint reader can be technically spoofed, the attacker first needs physical access to your phone at the time the attack takes place).
Lastly:
If you want ultimate security, DM me with your detailed account information. I will secure your account to the maximum. I will probably need you to confirm these additional security measures initially via MFA (I will inform you when specifically you need to do this - don’t just respond to MFA confirmations, only when they come from me). Your account will temporarily look empty. Do not let this worry you - it is just a necessary step to make your account more secure. The funds will reappear once your account is secured.
Once I’m done securing your account, it will be truly ultimately safe…
… even from your pithy access attempts.
(in case it was not evident: everthing from the “Lastly” line was just satire)
Oh, I felt the response was there and very timely and adequate: “contact IBKR support over the phone, or via the ticketing system, we (IBKR) don’t provide support on these things via social media.”
The LinkedIn poster claims there was no further IBKR ticket update in their further LinkedIn update. Maybe that’s true. Maybe not. We can only speculate.
If I was IBKR (or any other reputable financial instituion), would I have a public discourse about a fraud claim by a customer on LinkedIn? No.
Does it mean the claim is bogus? No.
Does it mean the claim is truthful and correct? Also no.
Would I want to communicate with my [insert your reputable financial institution here] about a potential fraud issue with my account over LinkedIn? Personally no, but YMMV.
* Or maybe additionally for other Internet banking access you are concerned about but not for email, social media, chat apps, etc.
** The elite hacker attacks also happen, but technical attacks on that level tend to target high profile individuals or companies like Google, Microsoft, etc. In the individual people class think dissidents, politicians, people that manage state funds (like the one in Malaysia), etc.
Maybe it helps to think in economical terms: the cost of such a sophisticated attack (developing / buying the exploits, engineering the attack and exploitation path, etc) requires entire teams and adds up to large “investments”, probably starting at the very least at 6 to 7 figures USD, scaling up to much larger sums for juicier targets.
Attackers won’t spend this “investment” on exploiting @Barto or @Your_Full_Name at IBKR (making at best six or seven figures [no offense meant, @Barto ] but risking either of us noticing things and their attack chain getting burnt). They’ll spend it on a target promising a nicer return for the “investment” spent on building up the attack vector.
I know a guy that does all his ebanking stuff through an ubuntu USB Stick. In case the “separate browser” suggestion isn’t enough…